- About
- Network
- Community
- Initiatives
- News
- Events
- Blog
- Publications

Minding Our MANRS: CENIC and Global Internet Routing Security
Categories RENS & NRENS Security Technology & Innovation
The origins of the modern Internet stretch back decades to a time when everyone on the network knew one another and valued the uses to which it was put. It supported a tight-knit global community and was used by researchers who were as familiar with one another as with its informal rules. They had no reason to transgress these rules, as their research depended on the Internet’s function.
Today, the Internet stretches around the globe and supports not only esoteric research but also the foundations of society, including finance, health care, government and defense, employment and education, and entertainment. It also supports the activities of those who would undermine these structures, be it for illegal profit, to sow social or political disorder, or simply as the result of an accident. One famous example of such an accident took place in 2008, when a Pakistan-based telecom company attempted to prevent its local customers from accessing YouTube by changing YouTube’s entry in its own local IP routing database to redirect any customer requests for access to the popular streaming platform. Unfortunately, this IP routing change propagated to other routers and switches around the world, effectively taking YouTube offline globally for several hours. More recently, in February 2022, attackers hijacked addresses belonging to a South Korean cryptocurrency platform and then forced its customers’ computers to run malicious code housed on the attackers’ servers. This code misdirected the customers’ transactions and enabled the theft of $1.9 million worth of cryptocurrency.
Havoc can also result from the deliberate misdirection of Internet traffic, where data packets from a nefarious source are purposefully marked with a false source address and prompt many innocent recipients’ computers to bombard the equally innocent false packet source with excessive data. This is the mechanism behind distributed denial of service (DDoS) attacks against false source addresses, whose servers buckle under the sudden avalanche of data directed at them.
Had the routers and switches managing Internet traffic not accepted the Pakistani ISP’s IP routing change or the IP address hijacking of the aforementioned crypto hackers, these incidents would not have happened or would have been far smaller in scale. Similarly, ISPs can help prevent DDoS attacks by checking their customers’ packets to ensure that they are being addressed honestly.
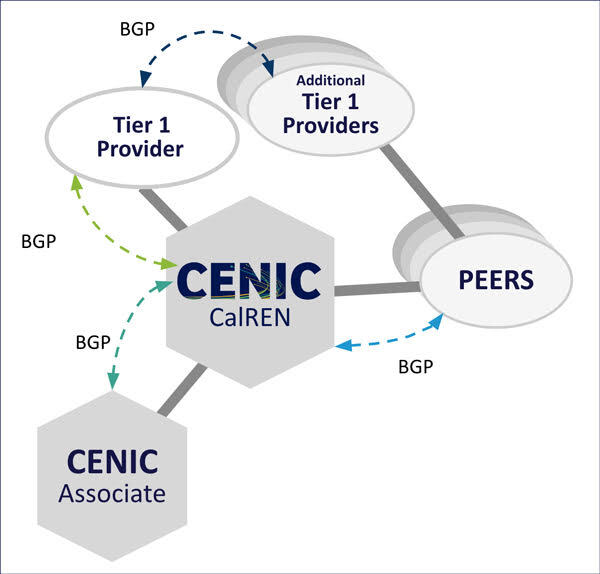
To this end, a consortium of ISPs and other commercial and nonprofit entities whose networks comprise the Internet has created the Mutually Agreed Norms for Routing Security (MANRS) initiative to address the most common ways in which network traffic can be incorrectly routed. By joining this initiative, CENIC has committed to collaborating with other participants and has agreed to share accountability for the global Internet routing system that controls network traffic flow. Participation involves the following types of activities:
The implementation of network policies to ensure the trustworthiness of any routing information originating on one’s own network, referred to as prefix filtering and anti-spoofing
Organizational participation in event response, maintenance of the IP address databases that underlie the Internet, and other activities that enable providers around the world to implement helpful policies on their own networks
A site connected to CENIC’s California Research and Education Network (CalREN) must advertise its own IP addresses in order to be globally reachable. As an example of prefix filtering, CalREN permits these sites to advertise only their own IP addresses, a policy that would have prevented the aforementioned telecom provider from improperly advertising incorrect IP routing for YouTube and kept those crypto-hackers from hijacking that cryptocurrency platform’s address. Furthermore, CalREN checks IP addresses advertised by sites connected to it against global address databases to ensure their accuracy. Routing advertisements that do not adhere to these rules are discarded by CalREN.
Anti-spoofing policies implemented on CalREN ensure that all data packets from CENIC’s downstream sites are sourced with the correct IP addresses, preventing them from impersonating other sites or carrying out DDoS attacks. Data packets found to contain incorrect source addresses are also discarded.
CENIC’s organizational participation in the MANRS initiative consists of ensuring that our own contact information is up-to-date so that engineers worldwide and from any service provider can contact us and coordinate incident responses. Our involvement also includes working to ensure the accuracy of the global address databases that underpin the Internet, thus enabling other service providers to implement their own filtering and anti-spoofing policies.
MANRS also offers tutorials, workshops, working groups, and events where representatives from networks, content delivery networks, cloud providers, IXPs, and equipment vendors can meet, share expertise, and ensure that the world’s most foundational infrastructure remains secure and able to support the critical activities of twenty-first-century society. More information can be found at MANRS.org.
Related blog posts
Pacific Wave Signs MoU with New Japan-Based Research and Education Exchange Facility FUJIXP
Pacific Wave, International Networks at Indiana University (IN@IU), and Coalition of Interoperable Networks for Japan (CINJI) and International have signed an MoU formalizing connectivity to FUJIXP, CINJI's new Tokyo-based open exchange facility for research and education networks.
The Big Game Is Big Data: How CENIC and the California Research and Education Network Support Member Athletics
When Fresno State needed to connect to Pac-12 Enterprises to broadcast a live football game over CBS, the Chancellor's Office reached out to CENIC for what Pac-12 later called the smoothest turn-up they've ever experienced.


