- About
- Network
- Community
- Initiatives
- News
- Events
- Blog
- Publications
DDoS Mitigation Services
CENIC Distributed Denial of Service Mitigation Service (DMS) Solutions: Managed and Self-Service DMS
CENIC is now offering its associates protection from Distributed Denial of Service (DDoS) attacks. Through CENIC’s Internet2 membership, CENIC is able to contract for Radware’s on-demand, cloud-based DMS. This allows CENIC members to purchase service through CENIC, leveraging Internet2’s attractive pricing and CENIC's high capacity, direct connections with Internet2 and through Internet2 to Radware.
CENIC has defined two levels of service: Managed DMS and Self-Service DMS. The two options are technically quite similar. With both options, mitigation is handled by Radware scrubbing centers located in the U.S., which have a total capacity of 2 Tbps each and support IPv4 and IPv6. This is an on-demand service that must be initiated when an event occurs. This is not an “always-on” service with continuous automatic protection from attacks.
As their names suggest, the options differ predominantly in who handles management of the “on-demand” aspect of the service. The following sections detail the key elements of each option.
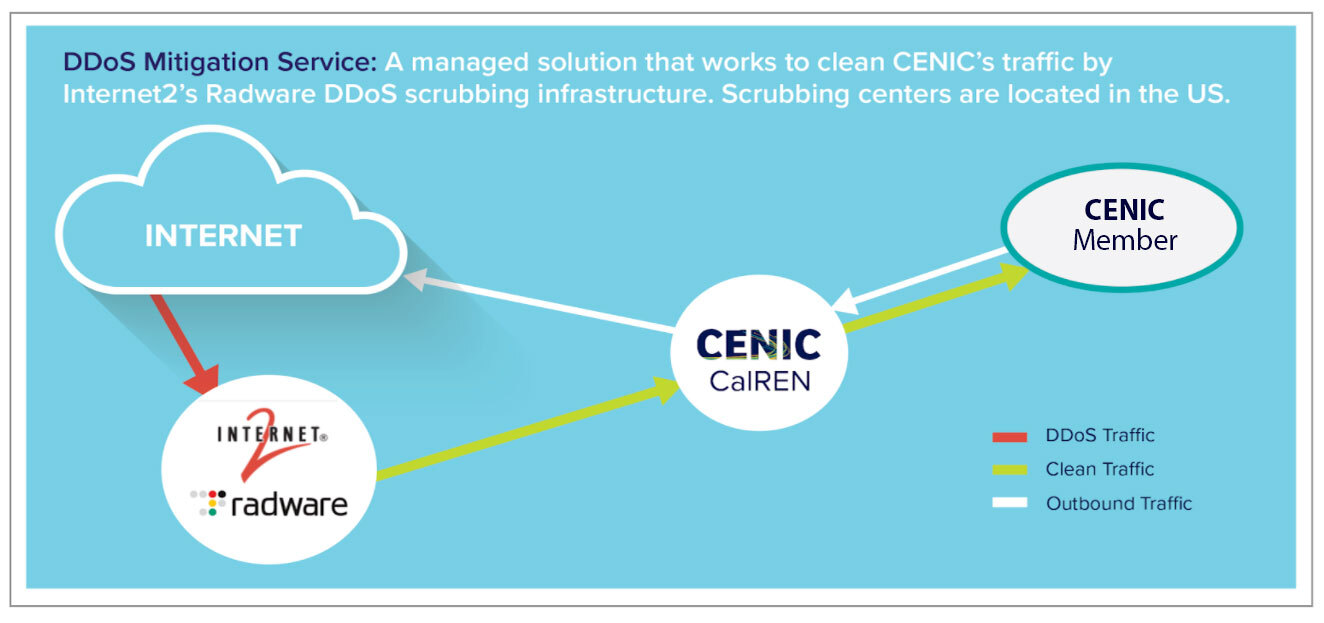
CENIC-Managed DMS
- CENIC will perform the technical setup for the CENIC-Managed DMS customer
- CENIC will monitor for and detect volumetric attacks that operate at the network and transport layer of the Open Systems Interconnection (OSI) model
- CENIC will activate and deactivate mitigation scrubbing services (upon customer approval)
- CENIC will provide quarterly reports of mitigation activity
- CENIC serves as the point of contact with Radware for this service
How CENIC’s Managed DMS Solution Works
CENIC has developed in-house tools to assist with DDoS detection and identification using NetFlow data that is continuously ingested from backbone interfaces. CENIC’s Operations team uses these tools to monitor and quickly identify potential DDoS attacks, taking appropriate actions on behalf of associates using this service.
When a DDoS attack is identified, Operations will request approval from the network contact at the DMS customer site before initiating mitigation. Once approved, Operations will adjust routing policies to shift traffic bound for that site to Radware, with all “clean” traffic coming through Radware’s scrubbing servers and returned to CENIC’s California Research and Education Network (CalREN) over the 4 Gbps connection that CENIC has established with Radware through Internet2. The service is capable of scrubbing /24 for IPv4 subnets and /48 for IPv6 subnets.
After a DDoS attack has ended and no further occurrences have been seen for 48 hours, a post-mortem report will be generated and provided to affected DMS customers.
CENIC Self-Service DMS
- Customer works directly with Radware’s Security Operations Center (SOC), with direct access to the tenant portal
- Customer is responsible for the technical setup of the DMS solution, with assistance from CENIC for CalREN portions of the setup
- Customer is responsible for developing processes and tools required to monitor for and detect DDoS attack activities
- Customer is responsible for monitoring and detecting attacks, and for activation and deactivation of the mitigation scrubbing services
DMS: What type of protection does it provide?
Radware’s DMS product mitigates volumetric attacks that operate at the Network and Transport layer of the Open Systems Interconnection (OSI) model. Therefore, protection is offered against DDoS attacks that target network infrastructure and equipment in an effort to overwhelm bandwidth and session handling capacity. DMS does not protect against other types of cyberattacks, such as ransomware/malware, SQL injection, and cross-site scripting attacks, all of which target Application layer vulnerabilities.
Process and Estimated Timelines
- Timeline estimates are dependent on associate availability and scheduling coordination for some portions of the process.
- DMS option selection by the associate
- Execution of contract documents between CENIC and the associate is dependent on the contracting process requirements for the specific segment interested in this service.
- Participation in a kick-off meeting for new DMS customers (one-hour meeting; scheduling of this meeting may introduce delays)
- Completion of onboarding documentation by the associate (dependent on associate)
- Processing of onboarding information by Internet2/Radware (two to five days, depending on the complexity of the network details provided)
- Configuration of CalREN and associate CPE to support mitigation (two weeks, depending on the associate’s change control process and availability to schedule and execute configuration changes)
- Validation (testing) of mitigation diversion and confirmation of production configuration (one-hour validation with a two-day lead time for scheduling, depending on associate’s availability to schedule)
Pricing
Complete the following linked form and CENIC will follow up with you about pricing and estimated timelines for the DMS solution for which you are interested.
FAQ
What is required to obtain DMS services from CENIC?
- Execution of contract documents between CENIC and the associate.
- Participation in a one-hour kick-off meeting for new DMS customers.
- Completion of onboarding documentation by the associate, which includes:
- Acceptance of Radware’s terms of service.
- Completion and submission of “on-boarding” forms (detailing customer administrative contacts, technical contacts, and in-scope network information).
- Letter of authorization (LOA) for Radware to provide technical mitigation support.
What is the difference between the CENIC Self and Managed Service offerings?
Associates who opt for the Self-Service solution will have direct interaction with Radware on mitigation while associates who opt for the Managed Service solution will rely on CENIC's expertise to handle mitigation with Radware on their behalf. In addition, the Managed Service also provides associates with additional monitoring from CENIC's network monitor tools by use of NetFlow analysis.
Is IPv6 supported?
Yes, both IPv4 and IPv6 are supported.
Is CENIC performing the scrubbing of DDoS traffic?
CENIC does not scrub any of the traffic. This is performed by re-routing all return traffic through Radware scrubbing centers that are located in Ashburn, VA, and San Jose, CA. Radware servers scrub DDoS traffic, and then clean traffic is returned to CENIC’s California Research and Education Network (CalREN).
What is the smallest prefix that can be diverted under a DDoS attack?
The smallest prefix that can be diverted for IPv4 is a /24 and for IPv6 is a /48.
How much does the CENIC DMS offering cost?
Complete the following linked form and CENIC will follow-up with you about pricing and estimated timelines for the DMS solution for which you are interested.- DMS Inquiry Form
Is the service “always on?”
This is not an "always-on" service since normal traffic is not always being routed and scrubbed through Radware servers. When a DDoS attack has been identified, traffic will need to be diverted into the scrubbing centers by making routing changes on the devices.
Who do I contact if my organization believes we are experiencing an attack?
Information on contacting us by phone or email.
If you believe that you are experiencing an attack, please contact the NOC by phone at (714)-220-3494 or by email at noc@cenic.org. Operations engineers can validate and identify the attack using network tools, as well as initiate diversion into the scrubbing centers if needed.
How is my organization’s traffic affected during DDoS mitigation?
Mitigated traffic is diverted towards the Radware scrubber and then back to your site, but the overall impact on traffic should be transparent. In other words, end-users should not notice any difference between normally routed traffic and mitigated traffic.
What is the total scrubbing capacity offered by CENIC?
The total scrubbing capacity is currently 4 Gbps. This capacity is shared between both the Self and Managed Service offerings. The 4-Gbps limit is not a hard cap and is capable of bursting higher if needed. CENIC engineers will analyze normal traffic usage patterns for a /24 being mitigated before diverting. Diversion will also be dependent upon the number of participants actively mitigating at that time.
Is traffic scrubbed in the US or offshore?
Radware has scrubbing centers established worldwide with a total capacity of 7 Tbps. Traffic from CENIC will only be scrubbed within US-based scrubbing centers that are located in San Jose, CA, and Ashburn, VA. These two scrubbing centers have a combined capacity of 2 Tbps.
How is our traffic re-routed to Radware?
Traffic is re-routed to Radware by tagging traffic with a specific BGP community. For the Managed Service offering, CENIC engineers will reconfigure devices to tag specific prefixes with the Radware scrubbing community in order to divert traffic. For the Self-Service offering, the campus will need to tag the prefixes at their border devices in order to initiate diversion into Radware scrubbing centers.
Will a report of what occurred during a DDoS attack be available?
Yes. Once the attack has ended and no further attacks have occurred for 48 hrs, CENIC will begin its process of closing out the case, which includes compiling a summary of the attack.
Will my organization have access to tools to monitor a DDoS attack?
The tools used by CENIC operations are not available to associates. These are internal tools only that CENIC has developed in-house to support not only DMS services, but other applications within the CENIC network environment.
What are the technical requirements to receive CENIC DMS services?
Associates will need to be directly connected to CENIC’s network.
Can I contact someone to further discuss the DMS offering?
Complete the following linked form and CENIC will follow up with you: DMS Inquiry Form
Can DMS protect me against malware and ransomware?
Cyberattacks such as ransomware/malware, SQL injection, and cross-site scripting attacks that target application-layer vulnerabilities would not generally be protected by DDoS mitigation techniques.
Will CENIC monitor my traffic for any potential DDOS attacks?
Subscribers of the DMS Managed Service will be set up to generate alerts to the NOC when there is a potential DDOS attack. Associates are also encouraged to contact the NOC when they suspect there is an attack happening to their site so CENIC engineers can investigate further.
What type of protection does CENIC's DMS Service provide?
Radware’s DMS product mitigates volumetric attacks that operate at the network and transport layer of the Open Systems Interconnection (OSI) model. Therefore, protection is offered against DDoS attacks that target network infrastructure and equipment in an effort to overwhelm bandwidth and session handling capacity. DMS does not protect against other types of cyberattacks, such as ransomware/malware, SQL injection, and cross-site scripting attacks, all of which target application-layer vulnerabilities.
Does the service protect against cyberattacks or ransomware?
DMS does not protect against other types of cyberattacks, such as ransomware/malware, SQL injection, and cross-site scripting attacks, all of which target application-layer vulnerabilities.
How is traffic mitigation activated for the Managed Service?
When a DDOS attack is detected by CENIC’s detection tools or is reported by the site, the CENIC operations team will reach out to the site to request approval for activating mitigation. If the DDOS attack has an impact on the CENIC’s backbone, the CENIC operations team will activate mitigation prior to reaching out to the site for approval.
Can sites activate traffic mitigation?
- Yes, for the Self-Service solution.
- No, for the Managed Service solution.
What is the delay between the activation of the mitigation process and the actual DDOS mitigation of my traffic?
Nearly immediate; in the order of seconds.
When my traffic is on the DDOS protected path, is there an impact on my performance?
There is no impact on performance.
Can I use the service if I have a connection with CENIC and with another provider?
Yes. For the service to be most effective, the path through CENIC needs to be configurable as the best path.

